In this chapter, we list the comparison on computation cost of the cloud for file upload between … and our scheme.
Computational Cost
Data access issues in the field of the cloud computing provide a good measurement-based performance as mentioned along this research, and hence, the security features can be improved using the new proposed model as well as a suitable computational cost. However, the proposed protocol provides these advantages and evaluates the performance based on computational cost and security requirements.
The performance of our proposed scheme is evaluated using the existing experimental in [33] [34] [35] for a variety of cryptographic operations using MIRACLE [36] in PIV 3 GHZ processor with Windows XP operating system and 512 MB memory. From [33] [34] [35] the relative running time for the operations we adopted in our proposed scheme and we define some terms for the running time calculations:
Tp= Pairing operation= 20.01 ms
Th= Hash function= 3.04 ms
Tpm= Pairing-based scalar multiplication= 6.38 ms
Tec= ECC-based scalar multiplication= 0.83 ms
Other operations: omitted
The following tables illustrates the performance efficiency based on running time which is focus on user side including data owner:
Table 1: Computational Cost-based Performance Efficiency
|
Phases↓ |
Operations |
Running time (ms) |
|
Key Generation |
Tec+2Th |
6.91 |
|
Upload |
Tp+Th |
23.05 |
|
Download (Transformation Key) |
Tpm |
6.38 |
|
Total |
Tp+ Tpm+Tec+3Th |
36.34 |
The following table shows comparison between [37] [38] and our scheme in the major process which is file upload/download, with file in any size (not affected) and for one user:
Table 2: Comparison of Computational Cost-based Performance Efficiency
|
References→ |
Ref [37] |
Ref [38] |
Our scheme |
|
Upload |
872.09 |
33.24 |
23.05 |
|
Download |
400.21 |
39.25 |
6.38 |
|
Total |
1272.30 |
72.49 |
29.43 |
From the above tables we clearly can observe that our proposed model is more efficient and has low running time indeed. The following figure can simplify this comparison:
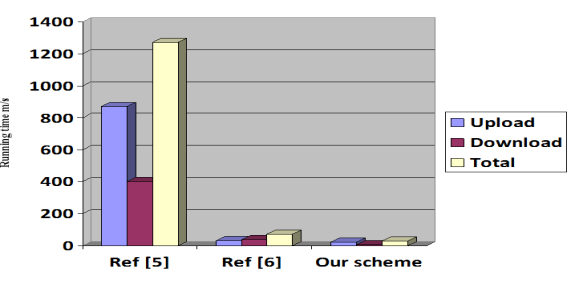
Figure 1: Comparison of performance efficiency-based running time

Security requirement
In the security aspects of our proposed model, we can notice that this model can achieve AC, FR, DC, IG, security requirements. Furthermore, this model not only provide a cost-based efficient scheme, but also provide a high secure and robust model against attacks such as Anti-collusion, Replay, MITM, and DoS attacks as follows:
Anti-collusion attack Some unauthorized users or members whose attributes do not satisfy the access policy, they may also try to access the data by colluding together with other users or even the service provider to compromise some data owner’s privacy. Our scheme is considered it to be secure against this attack due when a user is revoked, the group manager updates the revocation list (RL) stored in the cloud with a new. In addition, the group manager adds a time stamp to the data files and signs, to make sure that the cloud updates the data files.
New DF = sign ts (ð‘Ÿð‘˜ =(⟨𑢖,ð‘ƒ(ð‘¢–)⟩ ∀ð‘¢-∈ð‘…ð¿), group id, CT )
Replay attack Replay attacks are network attacks in which the attacker spies the conversation between the sender and receiver and takes the authenticated information e.g. sharing key and then contact to the receiver with that key. Moreover, our scheme is considered it to be secure against this attack due to temporary session by using timestamp for encrypted data.
Man-in-the-Middle Attack (MITM) Man-in-the-middle attack has become quite popular in the SaaS environment. Here the attacker intercepts the communication channel established between legitimate users and modifies the communication between client and server without their knowledge. Moreover, our scheme is considered it to be secure against this attack due to encrypted identities and the hash function used in the term of key generation:
Denial of Service Attack (DOS): Most of the serious attacks in cloud computing. In Denial of service attack an attacker prevent legitimate users of service from using the desired resources by flood a network or by consuming bandwidth .So authentication is need to distinguish legitimated clients from malicious clients, which can be performed through strong cryptographic verification. Moreover, our scheme is considered it to be secure against this attack due to the client creates a unique HMAC, or hash, per request to the cloud by combing the request data and hashing that data, along with his id and sending it as part of a request. The cloud receives the request and regenerates its own unique HMAC. The cloud compares the two HMACs, and, if they’re equal, the client is trusted and the request is executed.
Request | | tk+ H(id)
For convince, we define the following terms:
AC: Access control
FR: Flexible revocation
DC: Data confidentiality
IG: Integrity
Sym: Symmetric Algorithm
CT: Computational cost
TS: Timestamp
ODBE:
RBE: Role based encryption
LGS: leveraging group signature
DBE: dynamic broadcast encryption
Table 3 Security requirement comparison
|
References→ |
Ref [ 38] |
Ref [39] |
Ref [40] |
Our scheme |
|
Techniques |
Sym |
DBE |
RBE |
ABE |
|
Features |
AC, DC |
AC, DC |
AC |
AC, FR, DC, IG |
|
Comments |
High CT, No TS |
High CT, No TS |
High CT, No TS |
Low CT,TS |
|
Anti-collusion attack |
√ |
|||
|
Replay attack |
√ |
|||
|
MITM attack |
√ |
|||
|
DoS attack |
√ |
√ means the scheme can achieve the corresponding goal.
In general and from the above comparisons, our scheme can achieve data confidentiality, secure access control, integrity and flexible revocation. For clearly seeing the advantages of security of our proposed scheme, as explain in table 3, we list a table compared with ref [38], ref [39] and ref [40].
Delivering a high-quality product at a reasonable price is not enough anymore.
That’s why we have developed 5 beneficial guarantees that will make your experience with our service enjoyable, easy, and safe.
You have to be 100% sure of the quality of your product to give a money-back guarantee. This describes us perfectly. Make sure that this guarantee is totally transparent.
Read moreEach paper is composed from scratch, according to your instructions. It is then checked by our plagiarism-detection software. There is no gap where plagiarism could squeeze in.
Read moreThanks to our free revisions, there is no way for you to be unsatisfied. We will work on your paper until you are completely happy with the result.
Read moreYour email is safe, as we store it according to international data protection rules. Your bank details are secure, as we use only reliable payment systems.
Read moreBy sending us your money, you buy the service we provide. Check out our terms and conditions if you prefer business talks to be laid out in official language.
Read more