I. Webserver
We will be using apache web server in our project. The Apache HTTP Server Project is a synergistic programming improvement exertion went for making a hearty, business grade, featureful, and unreservedly accessible source code execution of a HTTP (Web) server. The undertaking is together overseen by a gathering of volunteers placed as far and wide as possible, utilizing the Internet and the Web to convey, arrange, and add to the server and its connected documentation. This undertaking is a piece of the Apache Software Foundation. Likewise, several clients have contributed thoughts, code, and documentation to the venture. This record is expected to quickly portray the historical backdrop of the Apache HTTP Server and perceive the numerous donors.
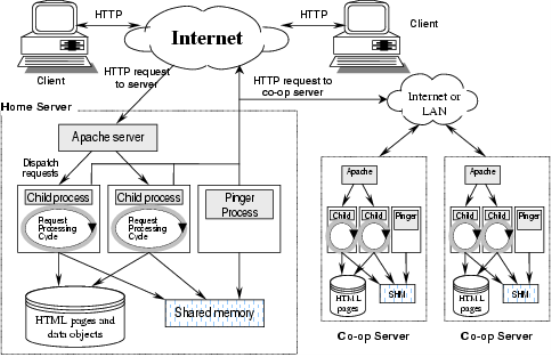
Figure 1. Apache General Structure.
In Figure 1 we can see the general diagram of apache webserver that how it will work and how it is connected in our scenario.
II. File Server
We will be using Turnkey as a file server in our project. A simple to utilize file server that joins Windows-good system file offering to a propelled online file chief and incorporates help for SMB, SFTP and rsync file exchange protocols. The server is designed to permit server clients to oversee files in private or open stockpiling. In view of Samba and AjaXplorer. This machine incorporates all the standard gimmicks in TurnKey Core, and on top of that:
1. SSL backing out of the case.
2. Webmin module for arranging Samba.
3. Incorporates mainstream squeezing help (zip, rar, bz2).
4. Incorporates flip to change over content file endings in the middle of UNIX and DOS groups.
5. Preconfigured wordgroup: WORKGROUP
6. Preconfigured netbios name: FILESERVER
7. Configured Samba and UNIX clients/bunches synchronization (CLI and Webmin).
8. Configured root as managerial samba client.
In Figure 2 we will show you that how file server is working in our project.

Figure.2 Internal connectivity of file server
III. Proxy server
There are many proxy server to choose but we have chosen Squid linex proxy server because it’s fast and secure.
The Squid Web Proxy Cache is a completely offered Internet storing server that handles a wide range of web demands for a client. At the point when a client asks for a web asset (website page, motion picture cut, realistic, etc..), their solicitation is sent to the storing server which then advances the appeal to the genuine web server for their sake. At the point when the asked for asset is come back to the reserving server, it stores a duplicate of the asset in its “cache” and after that advances the solicitation again to the first client. Whenever somebody asks for a duplicate of the “cached” asset, it is conveyed straightforwardly from the nearby proxy server and not from the inaccessible web server (contingent upon time of asset etc…).
Utilizing a proxy server can enormously diminish web scanning velocity if every now and again went by locales and assets are put away provincially in the cache. There are additionally monetary investment funds to be picked up in case you’re a substantial association with numerous Internet clients or even a little home client that has a portion remittance for downloads. There are numerous ways a proxy can be advantageous to all systems.
The squid proxy has such a large number of peculiarities, access controls and other configurable things, that it is difficult to cover the majority of the settings here. This section will give some fundamental setup settings (which is all that’s needed) to empower the server, and give access controls to keep unapproved clients from getting access to the Internet through your proxy. The design file has been archived greatly well by the designers and ought to give enough data to help your set up, however in the event that you don’t realize what a setting does, don’t touch it.
Since you have effectively arranged your Squid proxy server, you will need to arrange the majority of your workstations on your inward system to have the capacity to utilize it; this may appear like a long errand relying upon how enormous your inner system is. It likewise implies that you will need to physically arrange the greater part of your applications that unite with remote web servers for data/ information trade, this incorporates all web programs, infection redesign applications and other such utilities. Hmm, this could take a while.
One incredible gimmick of Squid is that is can be utilized as a HTTPD quickening agent, and when arranged in conjunction with an iptables sidetrack guideline, it will get to be straightforward to your system. Why? since we will no more need to setup the greater part of our applications on our workstations to utilize the proxy, now we can divert all HTTP asks for as they get through our firewall to utilize our straightforward proxy rather; less demanding organization.
A critical point before undertaking, straightforward intermediaries CAN NOT be utilized for HTTPS associations over SSL (Port 443). This would break the server to customer SSL association dependant upon your security and classifiedness of the protocol, it could likewise permit a “man in the center” assault due to caught (proxied) parcels.

Figure.3 Proxy server connectivity.
IV. DNS Server
At its most fundamental level, the DNS gives a dispersed database of name-to-address mappings spread over a progression
Of nameservers. The namespace is apportioned into a chain of command of areas and subdomains with every area managed freely
By a legitimate nameserver. Nameservers store the mapping of names to addresses in asset records, each having a related TTL field that decides to what extent the section can be stored by different nameservers in the framework. A vast TTL worth diminishes the heap on the nameserver however confines the recurrence of redesign engendering through the framework.

Figure 4. Basic DNS operation
Nameservers can actualize iterative or recursive questions. In an iterative inquiry, the nameserver returns either a response to the
Inquiry from its neighborhood database (maybe stored information), or a referral to an alternate nameserver that may have the capacity to answer the question. In taking care of a recursive inquiry, the nameserver gives back a last reply, questioning some other nameservers important to intention the name. Most nameservers inside the chain of importance are arranged to send and acknowledge just iterative inquiries. Nearby nameservers, on the other hand, commonly acknowledge recursive inquiries from customers (i.e., endhosts). Figure 4 delineates how a customer commonly discovers the location of an administration utilizing DNS.
The customer application utilizes a resolver, typically actualized as a set of working framework library schedules, to make a recursive inquiry to its nearby nameserver. The nearby nameserver may be designed statically (e.g., in a framework document), or rapidly utilizing conventions like DHCP or PPP.
After making the solicitation, the customer holds up as the neighborhood nameserver iteratively tries to determination the name (www.service.com in this case). The neighborhood nameserver first sends an iterative inquiry to the root to determination the name (steps 1 and 2), however since the subdomain service.com has been assigned, the root server reacts with the location of the legitimate nameserver for the sub-area, i.e., ns.service.com (step 3)1. The customer’s nameserver then questions ns.service.com and gets the IP location of www.service.com (steps 4 and 5). At long last
The nameserver furnishes a proportional payback to the customer (step 6) and the customer has the capacity interface with the server (step 7).
V. VPN and Firewall
We are using 2 types of VPN here.The first one is.
1. Site-to-site VPN – A site-to-site VPN permits multiple business locales in altered areas to make secure associations with each
Other over an open system, for example, the Internet. It additionally gives extensibility to assets by making them accessible to
Workers at different areas.
2. Access VPN – A remote-access VPN permits singular clients to build secure associations with a remote
PC system. These clients can get to the safe assets on that system as though they were specifically connected to the system’s servers.
Gimmicks in VPN
ï‚· Provide broadened associations crosswise over multiple geographic areas without utilizing a rented line.
ï‚· Improved security instrument for information by utilizing encryption strategies.
ï‚· Provides adaptability for remote work places and workers to utilize the business intranet over a current Internet
Association as though they’re specifically joined with the system
ï‚· Saves time and cost for representatives who drive from virtual working environments
ï‚· VPN is favored over rented line since leases are extravagant, and as the separation between business locales builds, the
Expense of rented line increment.
ï‚· IPsec VPN and SSL VPN are two arrangements of VPN which are broadly utilized as a part of WLAN.

Figure 5. VPN connectivity with our router.
As a firewall we are using IPtables. Iptables/Netfilter is the most prevalent order line based firewall. It is the first line of safeguard of a Linux server security. Numerous framework managers use it for calibrating of their servers. It channels the parcels in the system stack inside the bit itself. You can discover a nittier gritty diagram of Iptables here. Peculiarities of IPtables
1. It records the substance of the parcel channel ruleset.
2. it’s exceptionally quick on the grounds that it assesses just the parcel headers.
3. You can Add/Remove/Modify tenets as per your needs in the bundle channel rulesets.
4. Posting/focusing every standard counters of the parcel channel rulesets.
5. Helps Backup and reclamation with documents.
In this project there was so much stuff to learn about we have seen so many different kind of servers and it was difficult to decide what which server we should use Microsoft or Linux but we have seen in most of the cases Linux server were free and also very secure so we thought we will be using Linux server and In this project we have designed a perfect network design which is flawless. In figure 6 we have shown our whole network design.

Figure 6. Complete Network Design.
.
Acknowledgment
We are really grateful to complete our project with the time given by our professor Dr Hassan Raza. This project cannot be completed without the efforts and contribution of my group partner. We also thank our professor Dr Hassan Raza for his guidance.
References
[1] P. Mockapetris, “Domain names – concepts and facilities,” Internet Request for Comments (RFC 1034), November 1987.
[2] Paul Albitz and Cricket Liu, DNS and BIND, O’Reilly and Associates, 1998
[3] Weili Huang and Fanzheng Kong. The research of VPN over WLAN.
[4] CarIton R.Davis.The security implementation of IPSec VPN [M] .
[5] Baohong He, Tianhui. Technology of IPSec VPN [M]. Beijing: Posts & Telecom press, 2008, 7.
[6] NetGear VPN Basics (www.documentation.netgear.com/reference/esp/vpn/ VPNBasics-3-05.html)
Delivering a high-quality product at a reasonable price is not enough anymore.
That’s why we have developed 5 beneficial guarantees that will make your experience with our service enjoyable, easy, and safe.
You have to be 100% sure of the quality of your product to give a money-back guarantee. This describes us perfectly. Make sure that this guarantee is totally transparent.
Read moreEach paper is composed from scratch, according to your instructions. It is then checked by our plagiarism-detection software. There is no gap where plagiarism could squeeze in.
Read moreThanks to our free revisions, there is no way for you to be unsatisfied. We will work on your paper until you are completely happy with the result.
Read moreYour email is safe, as we store it according to international data protection rules. Your bank details are secure, as we use only reliable payment systems.
Read moreBy sending us your money, you buy the service we provide. Check out our terms and conditions if you prefer business talks to be laid out in official language.
Read more