a) i)












































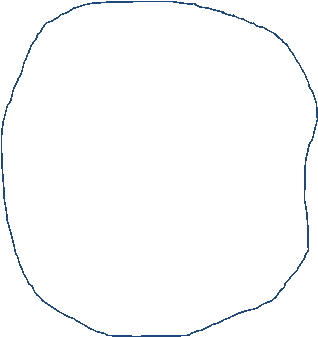















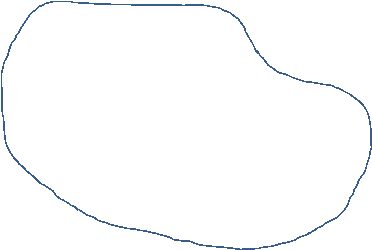





I have drawn a Systems map for the ‘Network Upgrade for Walgreens Boots Alliance’s European Business’.
I have picked key subjects as sub systems such as Customers, Contracts, Network (subbed into Improvements, access technologies and Traffic) and the Transformation Programme itself. I grouped them in this way; as the network upgrade formed the main part of the IT transformation programme which affects the Customers (Stores, centres, etc).
I included the ‘Customers Changing Health and Beauty Needs’ in the environment as these do not form part of the system; but only influence it.
By drawing the systems map I could see how many components needed to work together to produce an interconnected project to upgrade to a new IT system; thus showing the structure.
ii) I changed the Systems map into a T-O-P diagram, forming new groups and subjects which suited technologies, organisations and people.
I grouped companies into the organisation area, subgrouping them into other organisations. The technology area utilizes the Access Technologies part of the systems map, and the people area shows any influences in the case study from a person perspective.
By drawing the T-O-P diagram I could see how many components needed to work together to produce an interconnected project to upgrade to a new IT system. It shows a simple framework of the components of a sociotechnical IT system.

































































b)
In about 150 words describe a key element of ETHICS which could have been applied when analysing the IT system described in the case study.
ETHICS is all about participation. The Walgreens Boots Alliance has a strategy and programme in place to create a suitable network infrastructure; however I believe that there wasn’t any participation from end users or employees at the consultancy phase. The users could have given BT useful information and feedback regarding the current systems in place for customer service; thus participating in its design with technical and organisational aspects. The case study does not display or mention any information regarding any input from the company’s employees.
Establishing a design group at the beginning of the project with representatives from Boots, Alliance Healthcare and BT; including employees from different sections, grades and sex would put the project in a good starting position and show an element of ETHICS in operation.
A management change process should have been followed with formal documentation and signatures from various representatives to give the best sociotechnical solution for the system.
[153 words]
c)
In about 150 words, suggest and describe at least three issues of power between at least three of the key stakeholders in this IT system.
I have identified three stakeholders; these being Emer Timmons for BT, Erwin van Vroenhoven for Walgreens and the Customers themselves.
Emer Timmons (BT) has the power over the whole of the Walgreens Boots Alliance as he will set the strategy and the connectivity mediums for new technologies.
Erwin van Vroenhoven for Walgreens has the power over Alliance Healthcare and Boots to show the strategy of the alliance and is driving digital innovation for its future.
The customers are a significant stakeholder as they are the ones on the reciving end of the Technology and organisational changes of the alliance. The customer service is a key component to all the change and the customer has some power in defining the direction this moves in. The ever changing needs of a customer also influence the alliance’s strategy.
[135 words]
a)
METHOD is a process to accomplish a task with a systematic approach. For any successful Information Technology system; a clear vision is required with a precise method to implement it and a logical installation plan. Put simply a method can assist an initial idea or thought into a reality.
Method is extremely important with linking the idea to a reality and is the central focus point of an IT project.
Method needs to be capable of adapting, planned and designed in order for it to be a successful for an IT project.
b)
Making use of Agile, Multiview or SSM, suggest, in no more than 400 words, how this particular method could be applied to a specific project which you are familiar with, either from personal experience or from the literature.
In our company department we developed a piece of software using a database for high level planning (like a KANBAN style). Our team felt like each individual did not what each other was doing in a broader scale and looking at the bigger picture. We could use an AGILE method based approach to develop the software tool, we would review it, have feedback meetings, make changes, and follow a development cycle in order to get the planning tool we require.
Without this; the tool could be designed incorrectly and not focus on the user’s needs. The AGILE method focusses on people; and not technology and processes; showing that full participation if vital for its success.
This AGILE diagram taken from the adfkickstart.com (1) website; shows the basic process cycle that could be adopted for our software tool.

References
(1)adfkickstart. (2012). Agile Methodology. Available: http://www.adfkickstart.com/agile-methodology. Last accessed 7/2/2017.
Development stages would be the initial building of the tool with added functionalities with input from our team. The software would then but put on our live production system for feedback and a review stage.
The software would be either accepted or rejected. If the software is rejected, any changes would be recorded in a management of change process with adjustments and features determined.
Any further requirements would be taken onboard and follow the same cycle until the release of the software is met again. If the software is accepted then this would be the live and released version of the software.
This AGILE cycle would fit in with us for a number of reasons. It is difficult to predict the number of changes in the software requirements as well as the priorities. We did not know how much design work was needed and we did not know the amount of required time for analysis, design, construction and testing.
Using AGILE, we could focus on the users need; using initial meetings and consultation before developing a beta version. The AGILE method of work could give us this initial consultation and development we required; and its method is very useful for small scale software projects which are not mission critical. AGILE is ideal for proof of concept and not a large scale project; and could help our team with this planning tool very nicely. The idea was for the tool to be shared around other offices for high level planning and eventually get it developed by a software company to make it more rigid and standardised.
The AGILE method could let us improve our application, getting the end users feedback and ideas to re-engineer it and improve upon it to get a good experience for our department.
[435 words]
a)
An example of a system with Series reliability could be a circuit breaker and the electrical sockets on a ring main in a household. The circuit breaker can trip shut if it detects a problem with the circuit, which in turn stops all connected electrical sockets on that ring main to stop working.
An example of a system with Parallel reliability could be a set of water pumps at a power station where the first pump is set to run with maybe a couple of extra pumps on auto standby. If the first pump fails or does not generate the desired water pressure, a standby pump would start to make up the pressure.
Here is a reliability diagram for three components with reliability 0.92, 0.90 and 0.85 in parallel.



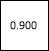





=1 – ((1 – 0.920) x (1 – 0.900) x (1 – 0.850))
= 1 – (0.08 x 0.1 x 0.15)
=1 – 0.0012
= 0.9988
=0.999 to 3 sf
This would mean the reliability of the system in parallel would be 0.999 to 3 sf.
b)
If a system has a mean time between failures (MTBF) of 1500 hours and a mean time to repair (MTTR) of 5 hours, what is its availability to two decimal places? Show your working.
(2 marks)
The availability A = MTBF / (MTBF + MTTR)
A = 1500/1505 =0.99667
Or A = 1.00 to 2dp
So the system is available 1.00 to 2dp
c)
In 200 words, explain why a system using two independently designed components can still fail.
Independently designed components in could still lead to a failure in a system. A system with independent components will need to be designed and specified correctly with compatibility and security features. If this is done incorrectly or the design has a fatal flaw; this could still lead to failure if a certain set of conditions are met. It can often be lots of small pieces in a bigger picture that can lead to a system failure.
If the design of the independent components is done correctly but an error has been made with software coding, firmware vulnerability or even a cyber security attack; the system could still face a failure. Coding is especially an issue with human interaction; leading to mistakes in the code and resulting in a malfunction of the system. Human interaction in general is a major failure point of even multiple independent components of systems; prime examples of this can be seen in the aircraft industry with the human interaction of alarms and displays.
Outside influences such as cyber security threats / attacks could lead to failure of individual components; or even something such with infrastructure such as a power outage / blackout.
[196 words]
a)
Explain the main features of Daniel Solove’s privacy model.
You should write no more than 100 words for this part of the question, and may include a diagram.
Daniel Solove’s privacy model divides privacy into four distinct ideas; these being information collecting, information processing, information dissemination and privacy invasion.
Information processing is the surveillance or interrogation of the data subject itself. This would extract some information or data which can be used for processing.
Information processing is about the storage and misuse of the data; using the data for secondary use and even excluding the data from the data subject.
Information dissemination is all about how the data is viewed; if the data use is misinterpreted wrong conclusions can be drawn from the data and the user’s purpose for it.
Privacy invasion is about the intrusion into people’s lives; the user may or may not be aware of the intrusion.
Solove’s model can be shown graphically this diagram















References
Jon Neiditz . (2016). Your Privacy Force Field for the Internet of Things. Available: http://datalaw.net/my-privacy-solution-for-the-internet-of-things/. Last accessed 05/02/2017.
[130 words]
b)
Explain three important challenges to privacy that someone involved in building or operating an IT system should be aware of. What would you conclude are the implications of these challenges for a systems administrator?
You should write no more than 100 words for this part of the question.
The first for an IT system is its overall complexity. Any user of the IT system will quickly realise how diverse and complicated a system can be with regards to privacy such as data, users, policies, etc.
Secondly; much of the data involved on the IT system has data collection, data processing, and invasion of privacy which is completely invisible to us. We do not know that is processing in the background and don’t have control of it.
Last of all; technological development with ever increasing social media applications and more smartphones (mobile) constantly changes the playing field regarding privacy and security.
In conclusion ensuring the security of systems can be extremely difficult and complex.
[115 words]
c)
Draft a note to your member of parliament explaining your support for, or your concerns about, the proposed legislation. With the aid of Daniel Solove’s analysis, focus your arguments on the government’s ‘nothing to hide’ claims. Outline two key reasons that Solove suggests the nothing to hide argument has ‘nothing to say’, and explain why you agree or disagree with him and the government’s approach with their CAT Act.
Note to parliament
I am very concerned about the proposed CAT legislation. Your ‘nothing to Hide’ claim is fraught with danger; using a Daniel Solove analysis “I don’t need to justify my position. You need to justify yours. Come back with a warrant.”
The ‘nothing to hide’ argument is focussing on 2 key elements; these being the disclosure of personal data or surveillance. What if the data collected is mistakenly identified as a criminal activity, or what if the data is leaked or stolen? The gartering of this data is distorted, as it will only pickup certain activities or traits; not looking at the bigger picture of the whole person.
I agree with Daniel Solove that the ‘nothing to hide’ argument has ‘nothing to say’ as it is too narrowly focussed on small pieces of privacy aspects. I think that the government should reconsider its position with pursuing this act.
M.Hermann
[150 words]
d)
Review your notes from the audio interviews with security experts Ross Anderson, Richard Clayton, Bruce Schneier and Duncan Campbell (see Block 2 Part 4, Section 4.5
Using those notes and your contribution to your tutor group forum (see Activity 4.15), explain whether each of the four might be in favour of or concerned about a law such as the CAT Act outlined in question 4(c).
You should write no more than 250 words for this part of the question, including extracts from your contributions to the tutor forums.
Your answer to this question should be no more than 600 words in total, plus one diagram.
Anderson states that people should be treat as humans with decency and respect; not just a raw material of data. He believes that data collected from people should have a consultation and feedback.
Andersonb would be behind an act such as CAT; as long as there is some open honesty from governments.
Schneier is concerned that our mobile devices and gadgets give away lots of information and that surveillance by governments and commerce is dangerous.
He believes that the security services are protecting us from the ‘bad guys’ using cyber security techniques; however he also believes that they are compromising our communications infrastructure.
I believe that Schneier would be strongly against a law such as the CAT act.
Clayton suggests that information used, should have some transparency. He says that users should be able to make the decision signing up to services that collect data.
Clayton points out about the power of metadata in preventing or solving crimes, however he also compares privacy and freedom.
I believe Clayton would be against the CAT act law.
Campbell has had first-hand experience with government surveillance; which led him to hi being prosecuted unfairly. Campbell believes the government has lost touch by operating in its own little world.
I think Campbell even with his own experiences would be behind an act such as CAT; however it would have to be ethical and regulated properly.
a)
Using your response to Block 2 Part 5, Activity 5.4
as a prompt, put forward two arguments for, and two arguments against, the use of professional codes of ethics.
(4 marks)
An organisations code of ethics show the overview of the integrity of the business by having core values. Cultures within companies that have built up ethical business practices engage stakeholders and gain trust with working relationships. A positive environment in the workplace is gained among employees inside the company; and also externally, trust gives a company good relationships with communities, customers and suppliers.
However; having a code of ethics does not necessarily mean that a company’s work place will adhere to it. There is no point in having a code of ethics that is not adhered to and engaged with. It is up to a company’s management and workplace to collaborate, educate and maintain conduct in their roles and responsibilities.
To add to this if a code of ethics does not have enough clear defined information, not installed and followed correctly or it is implemented in the wrong manner; a code of ethics can have a negative effect for the purpose it was intended for.
[165 words]
b)
To which of the normative ethical perspectives that were introduced in Block 2 Part 5, Section 5.2.3 do the following statements relate?
i.Virtue lies in taking the middle path between two vices.
ii.The greatest good for the greatest number.
iii.Some actions are inherently right or wrong, regardless of the consequences.
(3 marks)
i.Virtue lies in taking the middle path between two vices.- Virtue Ethics
ii.The greatest good for the greatest number.- Consequentialist Ethics
iii.Some actions are inherently right or wrong, regardless of the consequences.- Non-consequentialist Ethics
c)
Using your response to Block 2 Part 5, Activity 5.12(a) as a prompt, summarise the arguments for and against the proposition that organisations can be viewed as corporate actors rather than simply an organised groups of individuals.
(6 marks)
Organisations (these being groups that are organised for a common goal or purpose) can reach collective decision; however the opinion and ideas of individual can differ from these of the collective.
A collective or group could be held responsible for any decisions
To export a reference to this article please select a referencing stye below:
“Thank you UK Essays for your timely assistance. It has helped me to push forward with my thesis.”
If you are the original writer of this essay and no longer wish to have the essay published on the UK Essays website then please request removal.
Delivering a high-quality product at a reasonable price is not enough anymore.
That’s why we have developed 5 beneficial guarantees that will make your experience with our service enjoyable, easy, and safe.
You have to be 100% sure of the quality of your product to give a money-back guarantee. This describes us perfectly. Make sure that this guarantee is totally transparent.
Read moreEach paper is composed from scratch, according to your instructions. It is then checked by our plagiarism-detection software. There is no gap where plagiarism could squeeze in.
Read moreThanks to our free revisions, there is no way for you to be unsatisfied. We will work on your paper until you are completely happy with the result.
Read moreYour email is safe, as we store it according to international data protection rules. Your bank details are secure, as we use only reliable payment systems.
Read moreBy sending us your money, you buy the service we provide. Check out our terms and conditions if you prefer business talks to be laid out in official language.
Read more